Files are important for any software application. In the case of APPSeCONNECT, there might be a situation where the application starts performing weirdly because some files are deleted accidentally or by some anti-malware applications. In this article we will see, how we can audit file changes in a folder such that we can ensure the folders are accessed only by authorized application only.
Important locations?
In the case of APPSeCONNECT, there are mainly 3 locations to watch. The locations are marked as per priority.
- Program Files(x86)\APPSeCONNECT and its subfolders.
- ProgramData\APPSeCONNECT and its subfolders.
- User’s AppData\Local\APPSeCONNECT.
The first part contains files that should not be changed after all the processes are deployed and the project is in maintenance. These files are the basic installation files, which additionally add the Adapters based on the applications you are using.
The second file path is the location where all the important data is getting stored. This folder generally updates at regular intervals, because of the continuous execution of sync processes, but the number of files should not change over time during the maintenance phase.
The third folder is mainly the logs folder where all the logs are getting stored. These files are mostly unimportant but hold important logs to find out an issue. Here files will be created regularly, but we need to ensure the deletion does not take place unnecessarily.
How to know who deleted the file?
There are 3 steps that you need to follow to enable the auditing feature in Windows. Mainly we are concerned about the deletion of files, so in the example, we are going to show you how to quickly enable auditing for the deletion of files. Here are the overall steps :
- Enable File Auditing feature.
- Configure the folder to add File Auditing
- Verify the audit logs to find the culprit.
You need administrator permission to perform these operations, so if you see you are unable to do any of the operations, consult with your system admin.
How to enable File Auditing?
File auditing features are by default disabled in windows. To enable the feature, you need to set up certain group policies to ensure the feature is available. Here are the steps :
- Open Start -> Run, type “gpedit.msc” and press OK.
- The command will open Group Policy Editor.
- Select “Local Computer Policy” -> Windows Settings -> Advanced Audit Policy Configuration -> Object Access.
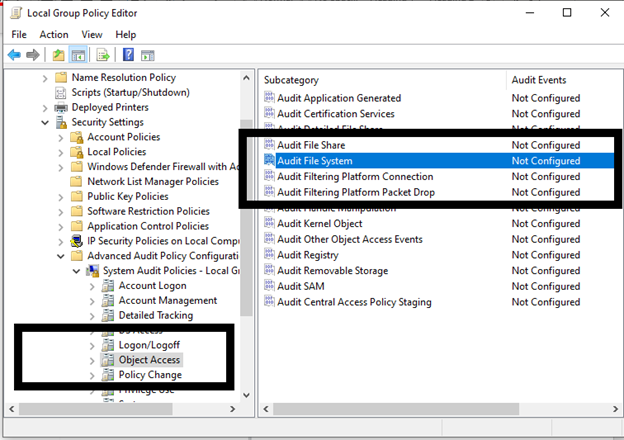
- Open Audit File System from the list of subcategories.
- In the audit file system properties window, Check to Configure the following audit events, and select both Success and Failure.
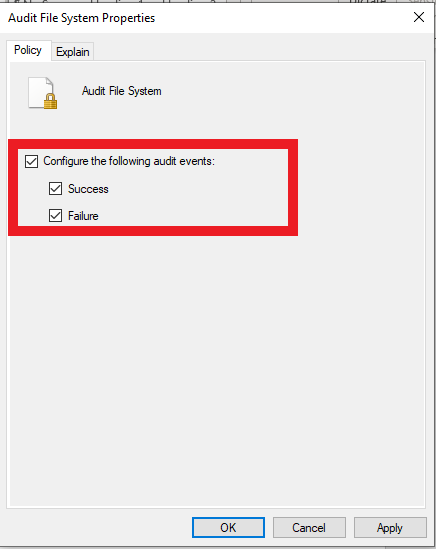
- Select Apply and Ok, then close the window.
After this step, the feature is enabled in your server.
How to Configure a folder to Start Auditing
After you have enabled the feature of auditing on a folder, it is time to start adding the rule. Based on our folder structure, let us consider putting it in the first folder.
- Open My Computer -> Go to Drive and Select Program Files (x86).
- Right-click on the APPSeCONNECT folder and select properties.
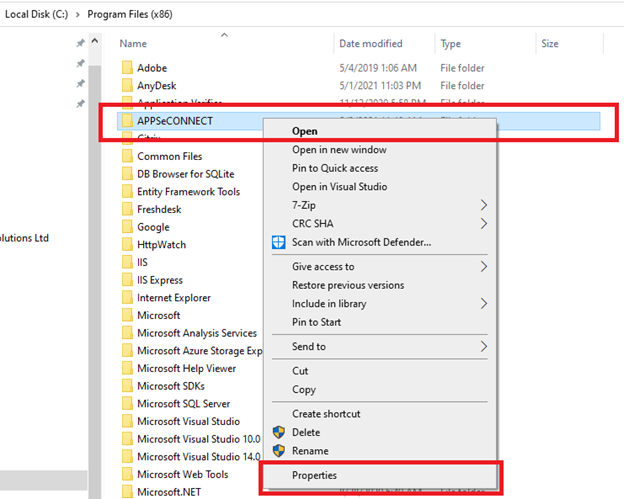
- In the properties window, select Security and then select Advanced.
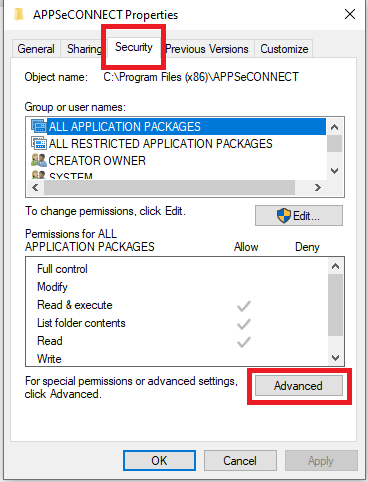
- In the “Advanced Security Settings” folder, select Auditing Tab and click Continue.
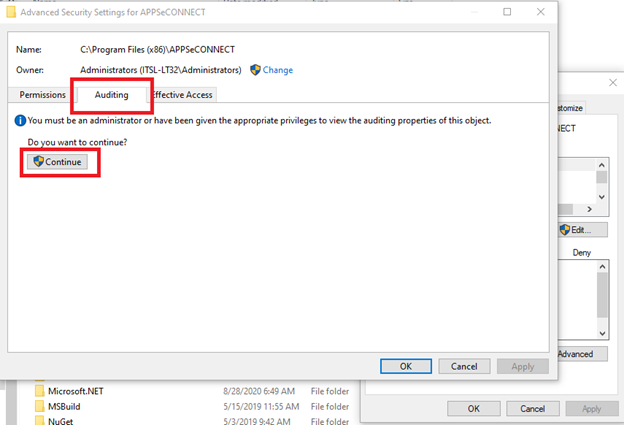
- Select “Add” to add a new policy.
- Select Principle and type in “Everyone” in the window. After you type in Everyone, do click on “Check Name” button to ensure it is properly picked.
- Once picked, click on “Show Advanced Option” and select “Delete subfolders and files” and “Delete” option.
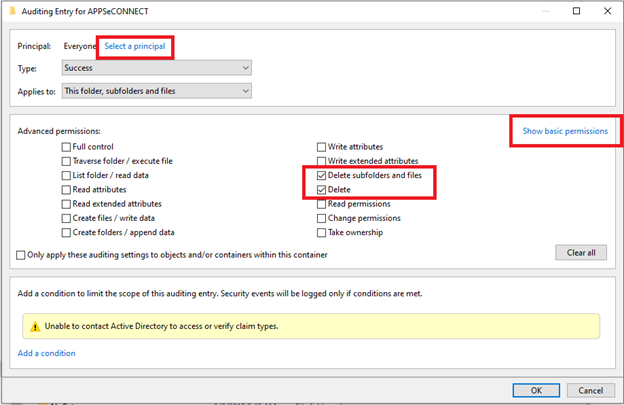
- Once you picked up these two options, you can press OK and apply the changes. Your folder will now be audited for any deletion.
Note, you can also add other audit policies in a similar way.
How to check logs?
The best part of this exercise is how you can check the logs.
- Open Start -> Run, select “EventVwr” and click Ok.
- Open Windows Logs -> Security.
- You will see “Audit Success” Entries.
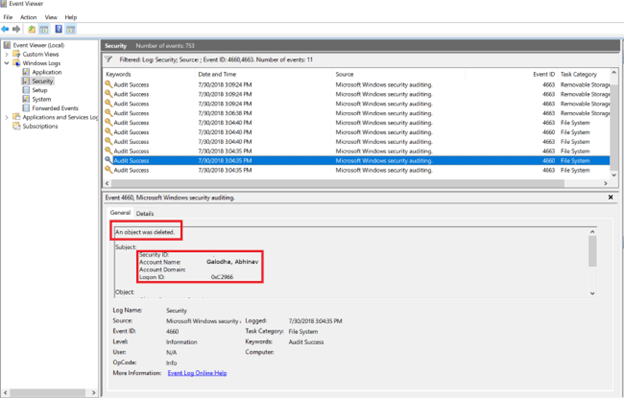
- You can filter out FileSystem Category with EventId 4663 using the filter menu to identify the entries which are deleted.
- Here in the entry, you will see which object is deleted, and also which executable deleted it. If you see “explorer.exe”, that means someone manually deleted the file.
- You can also identify the logged-in user which deleted the file.
Conclusion
This is an important consideration that you can configure to ensure you see the logs of any files getting deleted. APPSeCONNECT requires the files and folders to work properly, and any malpractice on the same will lead to fatal behavior, and to address such a scenario, you must understand which service is deleting files. This article helps you configure the system to generate logs when something suspicious happens on the file system.
Hope this will help you.
















